Introduction
If you want a fast STP review go check my previous post Part 1 for a foundation base for STP concepts and topics, now we are continuing deeper into the abyss.
Hopefully we will shed some light on the advanced features today.
List of features, super summary
Portfast: Put a port immediately into forwarding, good for edge ports.
BPDUfilter: Avoid to send or receive BPDUs on a port.
BPDUguard: If it see a BPDU, block the port.
Uplink Fast: Put an alternate path to the root immediately into forwarding.
Backbone Fast: When there is indirect failure, speed the convergence.
RootGuard: If you hear a better BPDU, block that port.
LoopGuard: If you try to put the port into Designated, block that port.
Portfast, BPDUfilter and BPDUguard: Best friends forever
Typically, you would want to enable all 3 features in the same ports, which are going to be edge ports.
Edge ports will be connected to end hosts, servers, printers…Anything but another switch.
Portfast: If you turn on a computer connected to a switch without Portfast, it will take 30 seconds to be operative just waiting for STP normal convergence timers.
DHCP will timeout and your computer will get an automatically assigned address like an APIPA from Windows. Now you have to open a ticket to get your issue resolved.
Another benefit of Portfast is more stable network, because every time a port goes into forwarding STP needs to inform the root that a change occurred, and then the root will ask all switches to flush their mac. Which is translated with a lot of ARP request and broadcast.
You can enable Portfast into an access port or even into a trunk port, but that trunk port must face a server(never a switch).
Notes:
- PortFast do NOT disable STP. Portfast ports still will send BPDU and listen to any incoming BPDU.
- If a Portfast port receives a BPDU it will become a normal port and lose all the Portfast benefits.
BPDUguard will help as an extra layer of protection for your edge ports. BPDUguard can block a frame or the whole port, if it receive a BPDU from the other end. By default will put the port into error-disabled status.
You can enable BPDUguard per port or globally, globally will affect just access ports.
You can enable auto recovery for error-disable ports after the BPDUguard action, or you can admin up the ports manually.
- errdisable recovery cause bpduguard
- errdisable recovery interval 30 (30 are seconds, you can set the number that you want above 30 s)
BPDUfilter will helps us to avoid unnecessary processing. End host do not need to hear about STP messges.
Imagine that you have a switch with 48 ports or one of the biggest chassis switches that can hold 380 ports. If you have 380 hosts, you have to send at least 380 BPDUs every 2 seconds for no reason. End host do not understand / care about STP messages.
Now imagine that you have 100 vlans, that´s 100 * 380 hellos every 2 seconds. Your CPU won´t be happy.
BPDUfilter, will stop the sending and receiving of BPDU in a port. Doing this is just disabling STP at 100%.
Enabling BPDUfilter at port level is dangerous, you are literally disabling STP and welcoming potential loops.
But there is a way to have all of our 3 advanced features all together working without disabling STP: enable all this processes at a global level, not inside a single port.
- spanning-tree portfast edge default
- spanning-tree portfast edge bpduguard default
- spanning-tree portfast edge bpdufilter default
Portfast will be enabled in all access ports, each one of that port will be protected by BPDUguard(if we receive a BPDU, port will be shutdown) and with the benefit of not sending BPDUs every 2 second.
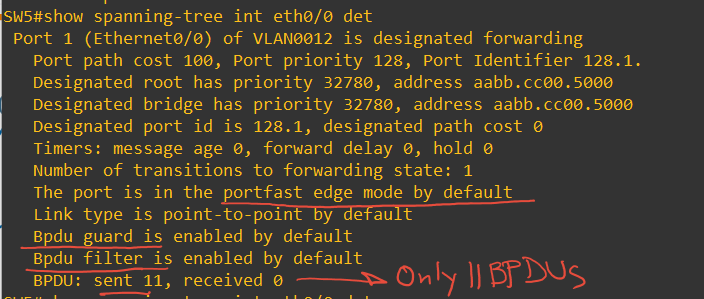
If you enable BPDUfilter at a global level, the switch will send 11 BPDUs to make sure there is no other switch in the other side; then it will stop sending BPDUs and SW will just listen for any BPDUs.
Uplinkfast and Backbone fast: Ready for all occasions
Uplinkfast is useful in direct failure scenarios, where the best Blocking port will transit into a root port as if it were an alternate path into the root.
A side effect of enabling uplink fast is that the switch will increase cost by 3000 and priority to 49152. This is done by default to avoid that switch to be used as a transit path in the future.
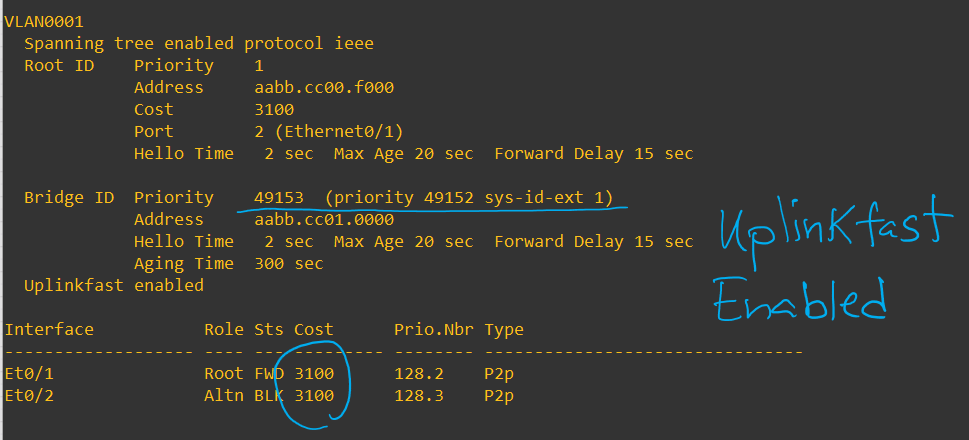
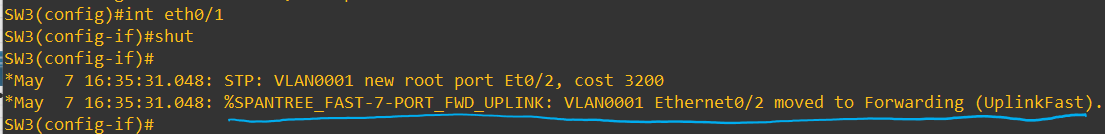
As you can see by having Uplinkfast, the port will go immediately into a forwarding Root port. We will skip the normal listening/learning timers.
Backbone fast, its used for indirect failures scenarios. In which a switch will lose a port and will believe for some time that it’s the switch root for a while. Let’s take a look:
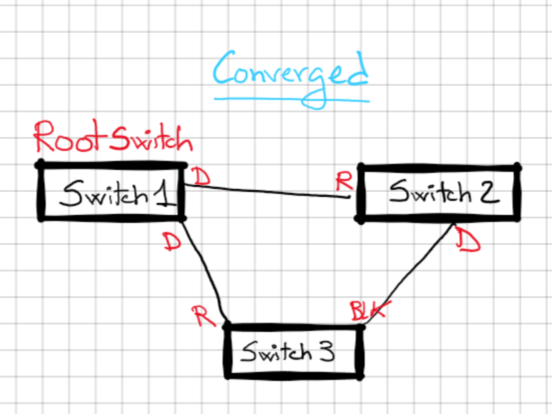
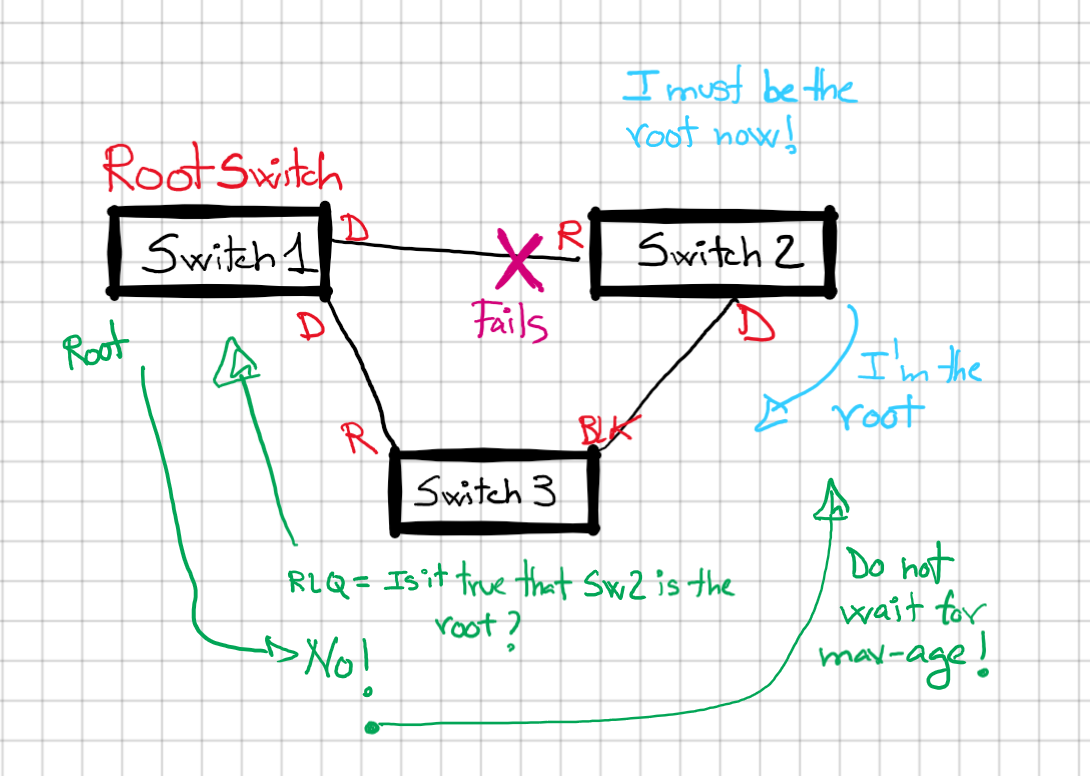
Backbone fast helps with an indirect failure, from SW3 point of view failure is indirect. SW3 start receiving BPDUs from SW2 claiming to be the root but SW3 knows the root is SW1. SW3 sends a RLQ(Root Link Query) to ask the root if still is the root; SW2 replies and SW3 tells SW2 do not wait for max-age as it that SW2 lost it’s root port.
Backbone fast saves us 20 seconds from Max-age, but still have to go through listening and learning to converge(30 s total).
Backbone fast must be enabled in all switches to work, as it is using special messages to deal with the indirect failures.
Rootguard and Loopguard: Choose wisely
You can only have one of the two enabled at the same time, hence the title. Actually, you don’t have to choose that much, as Rootguard will be enabled in the root and secondary root and Loopguard will go into access switches.
Example:
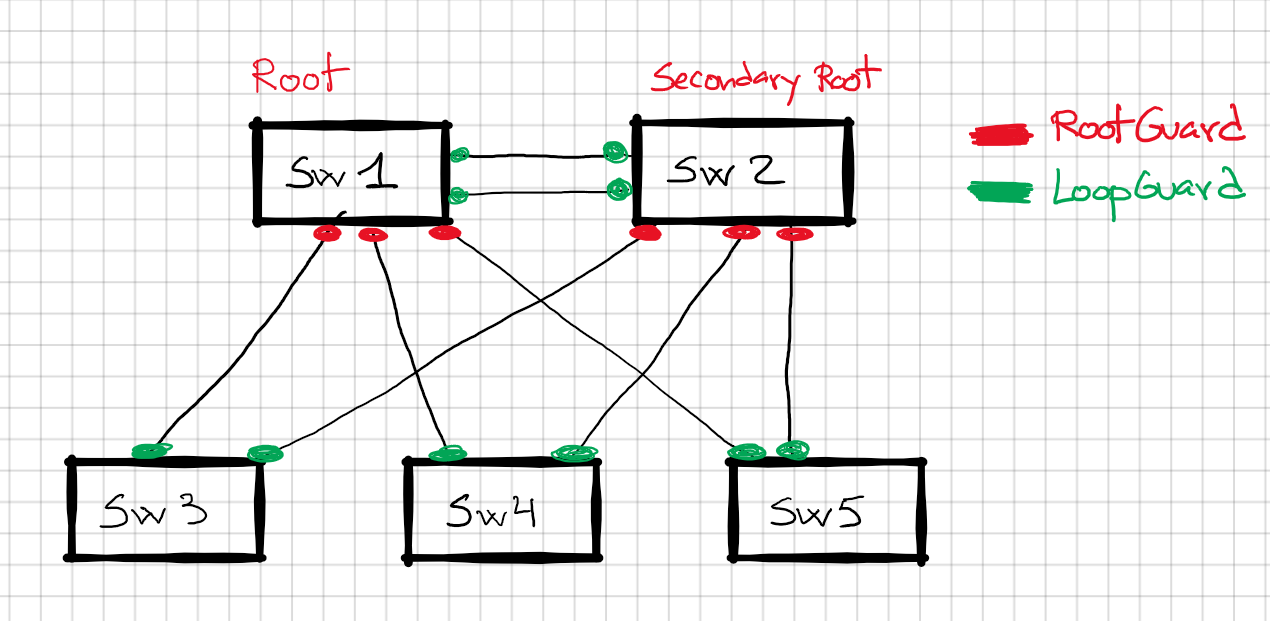
Rootguard: Avoids a port to become root, thus we have to enable towards the access switches 3-4-5 as they will never be root, we want to avoid our root switch to be moved to an access switch. If we prevent the Rootguard enabled ports to become root ports, our root switch will be safe. This makes sense if you think that Root switch will have always all its ports into Designated, so we want to avoid any port to change into a root port.
Loopguard: Used normally for fiber connections in the access layer, where you have a chance to lose the transmitting fiber and only listen BPDUs, if we don’t receive BPDU for the max-age timer the switch will move the port into Designated and we might have a loop. Thus, Loopguard avoids a non-root port to become designated, root ports are not affected by Loopguard; we can still have a root port per switch. We can use UDLD as an alternative method.
You cannot enable both at the same time, but you don’t have to. If you enable both, the last one that you put will take precedence.
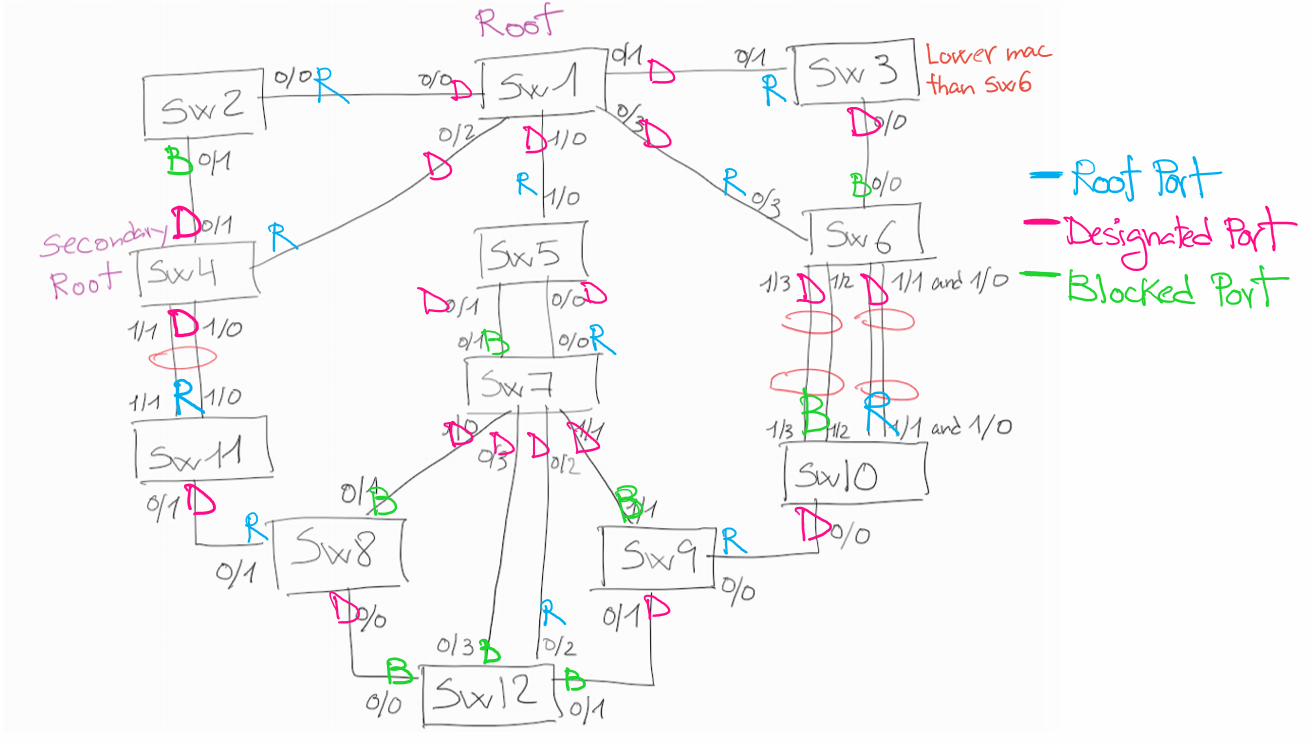
STP challenge resolved from last post
Here you go, last post challenge to set all ports resolved, note how port-channels between SW4-SW11 and SW6-SW10 have lower cost to the root, so they are selected as root ports.
Conclusion
We reached the last part of classic PVSTP+ advanced features, we talked about many stuff.
Later I’ll keep going with the Rapid PVSTP+ which includes many of the advanced features already built-in!
Any thoughts?




Recent Comments